October 24, 2025, Cybersecurity researchers warn that email phishing attacks have reached a critical inflection point this year, as threat actors deploy increasingly sophisticated evasion techniques designed to bypass traditional security tools and deceive even well-trained users.
According to new research from Secure list and other security firms, the phishing landscape in 2025 has evolved dramatically. Attackers are combining revived older methods with new delivery mechanisms that exploit weaknesses in automated scanning systems and human behavior
PDF Attachments Replace Links as Primary Attack Vector
Researchers have documented a sharp rise in phishing campaigns that use PDF attachments instead of traditional hyperlink-based lures. These PDFs often contain QR codes that, when scanned, lead users to malicious websites designed to harvest login credentials.
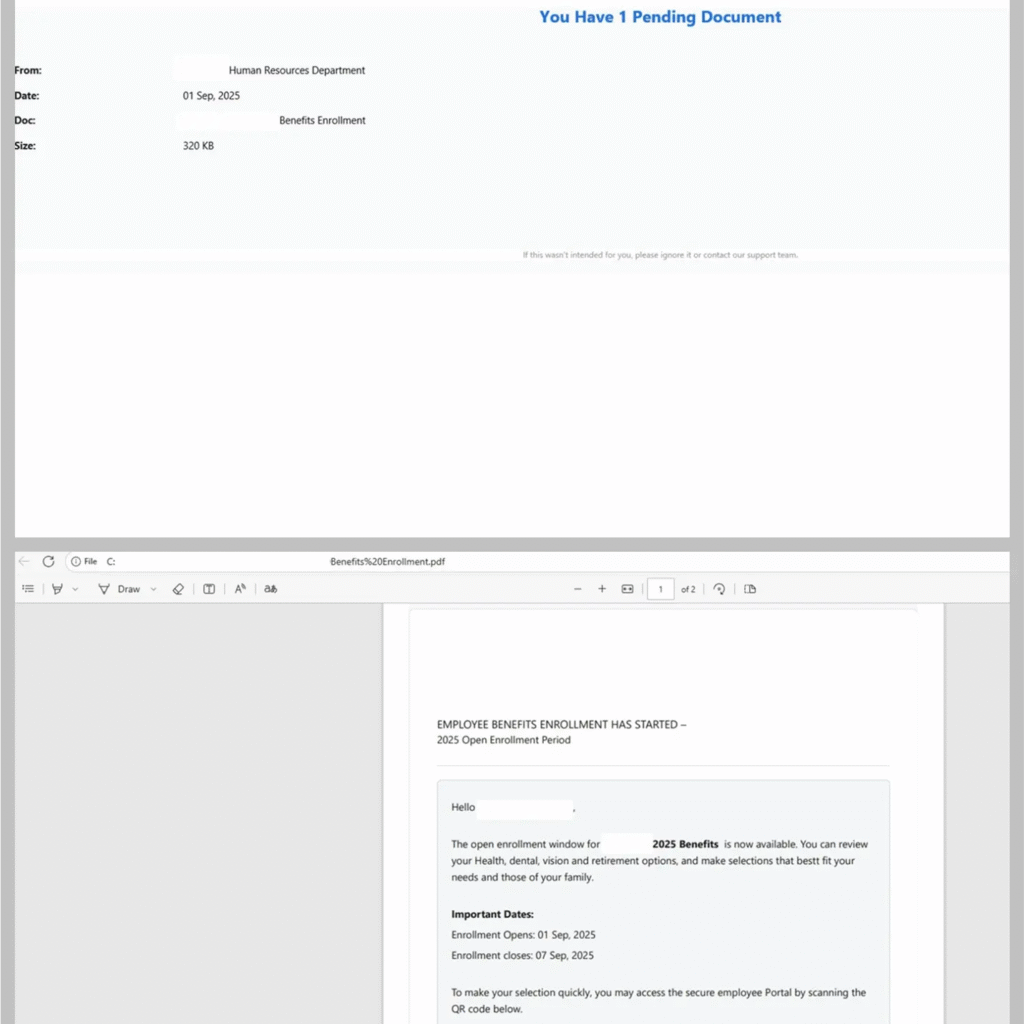
This shift allows cyber criminals to bypass email filters that scan for malicious links while encouraging victims to use mobile devices, which typically lack enterprise-grade security protections.
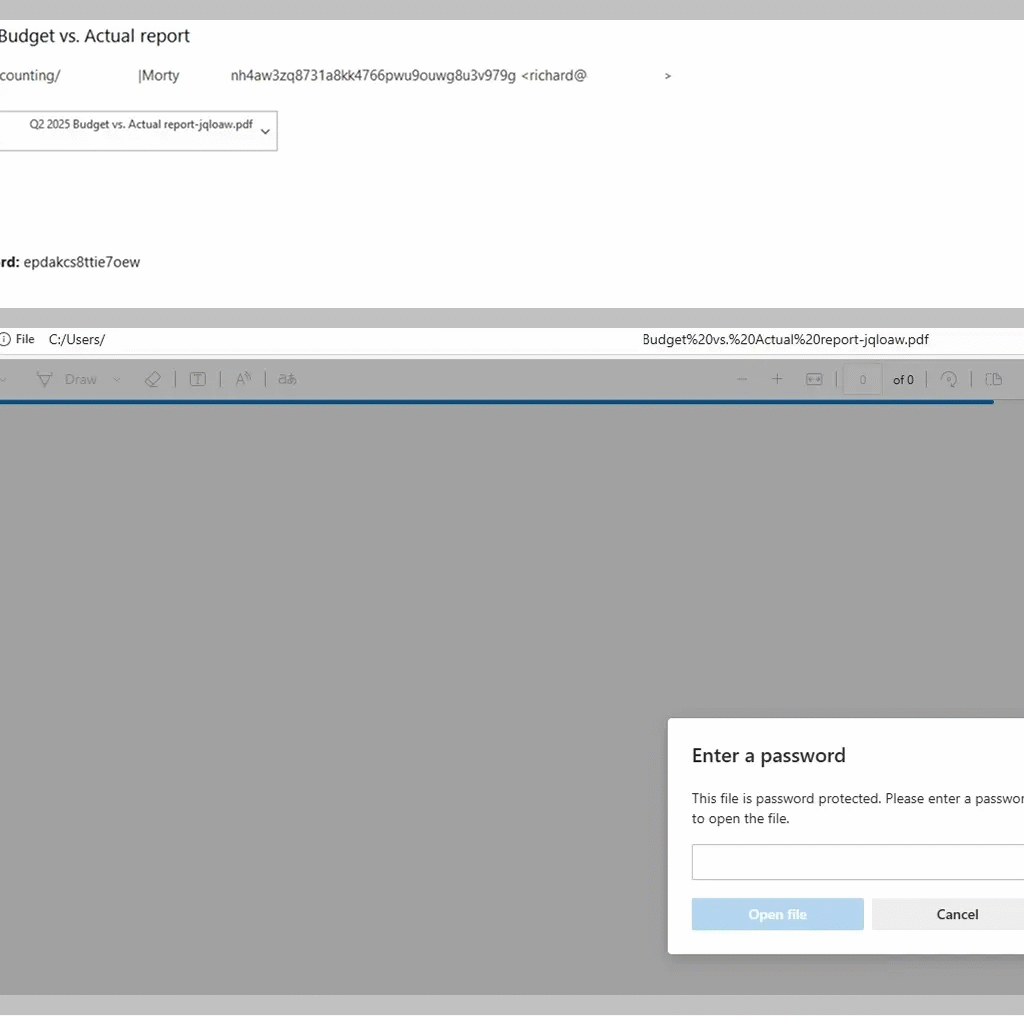
Secure list analysts report that these PDF-based phishing attacks have become more advanced, often using encryption and password protection to evade automated file scanning. In many cases, attackers send passwords in a follow-up message, a tactic that complicates detection and adds a false sense of legitimacy.
Security experts say this approach leverages psychological manipulation, mimicking corporate security protocols to increase user trust and compliance.
Calendar-Based Phishing Makes a Comeback
In a trend not seen since 2019, calendar-based phishing has re-emerged as a popular attack method. Instead of embedding phishing links in email bodies, cyber criminals insert them into calendar event descriptions.
Because calendar platforms automatically send reminders that often bypass email security checks, this strategy has proven especially effective in business-to-business (B2B) environments and corporate offices.
New Techniques Target MFA and Cloud Services
Phishing infrastructure in 2025 is more advanced than ever, with attackers implementing multi-layered evasion techniques that mimic legitimate authentication processes.
One increasingly common tactic involves CAPTCHA verification chains, requiring users to confirm they are human before proceeding to credential-harvesting pages. These CAPTCHAs frustrate automated scanners while preserving access for real users.
Researchers have also observed a surge in phishing campaigns targeting cloud storage and authentication services. In these cases, malicious websites interact directly with legitimate APIs in real time, mirroring the behavior of genuine login systems.
When victims enter their credentials, the phishing site communicates with the real platform, displaying authentic error messages and MFA prompts. This technique enables attackers to steal both passwords and one-time authentication codes, effectively bypassing multi-factor authentication (MFA).
Pixel-Perfect Phishing Pages Increase Realism
The visual fidelity of phishing pages has also improved. Attackers are now building pixel-perfect replicas of legitimate login portals, complete with corporate logos, folder structures, and interface details. These replicas make it nearly impossible for users to distinguish fake pages from real ones.
Once credentials are harvested, attackers can access accounts undetected, posing serious risks to businesses and individuals alike.
Experts Urge Layered Defense Strategies
Cybersecurity specialists warn that traditional email filters are no longer sufficient to counter these emerging threats. Experts recommend a multi-layered defense approach, including:
- Continuous security awareness training for employees
- Deployment of AI-driven email filtering tools capable of analyzing attachments and behavior patterns
- Enhanced monitoring of authentication activity to detect suspicious access attempts
“The phishing attacks we’re seeing in 2025 are far more adaptive and convincing than anything we’ve encountered before,” said a Secure list analyst. “They blur the line between legitimate and malicious activity and that makes user education and detection technology more critical than ever.”


Add a Comment