The notorious hacker group Mem3nt0 mori has once again made headlines, this time for actively exploiting a critical zero-day vulnerability in Google Chrome. This attack has caused a stir across Russia and Belarus, compromising high-profile targets with alarming precision. Known as CVE-2025-2783, the flaw in Chrome allowed these hackers to bypass the browser’s robust sandbox protections, leading to the deployment of sophisticated spyware on the victim’s machines.
Discovered by Kaspersky’s researchers in March 2025, the vulnerability was swiftly patched by Google. However, by then, the attackers had already used it in a series of well-coordinated cyberattacks. The attacks were part of a larger operation named ForumTroll, a campaign that targeted media outlets, universities, government agencies, and financial institutions. In this piece, we’ll take a closer look at how this attack unfolded and what it means for cybersecurity moving forward.
What is CVE-2025-2783?
CVE-2025-2783 is a flaw in Chrome’s sandboxing system that allowed attackers to escape its confines with minimal user interaction. Sandboxing is a security feature that isolates processes to prevent malicious code from affecting other parts of the system. However, this vulnerability circumvented Chrome’s sandbox defenses, enabling malware to run with elevated privileges and persist in the browser’s process.
The attackers exploited this flaw by crafting phishing emails that lured victims to malicious websites. When victims visited these sites, the exploit was triggered automatically — no downloads or clicks beyond the initial visit were required. This drive-by infection tactic is particularly insidious, as it leverages Chrome’s Mojo inter-process communication system, a key component responsible for managing data between browser processes on Windows.
The Technical Details Behind the Exploit
At the core of the exploit was a subtle logic flaw. Chrome’s code failed to properly validate certain pseudo-handles (e.g., -2, which refers to the current thread), allowing attackers to manipulate the system into duplicating handles across sandbox boundaries. This seemingly innocuous oversight was rooted in outdated Windows optimizations and proved to be a serious vulnerability.
By exploiting this flaw, attackers could execute shellcode within the privileged browser process. Once this access was gained, the attackers could deploy malware, ensuring persistence on the system by circumventing the browser’s sandboxing protections. In short, the attackers had found a way to inject malicious code into the browser’s core, enabling it to run with high-level privileges and evade detection.
The Attack Chain: How It Unfolded
Kaspersky’s Global Research and Analysis Team (GReAT) meticulously reconstructed the attack chain, which unfolded in several stages. Here’s how the attack worked:
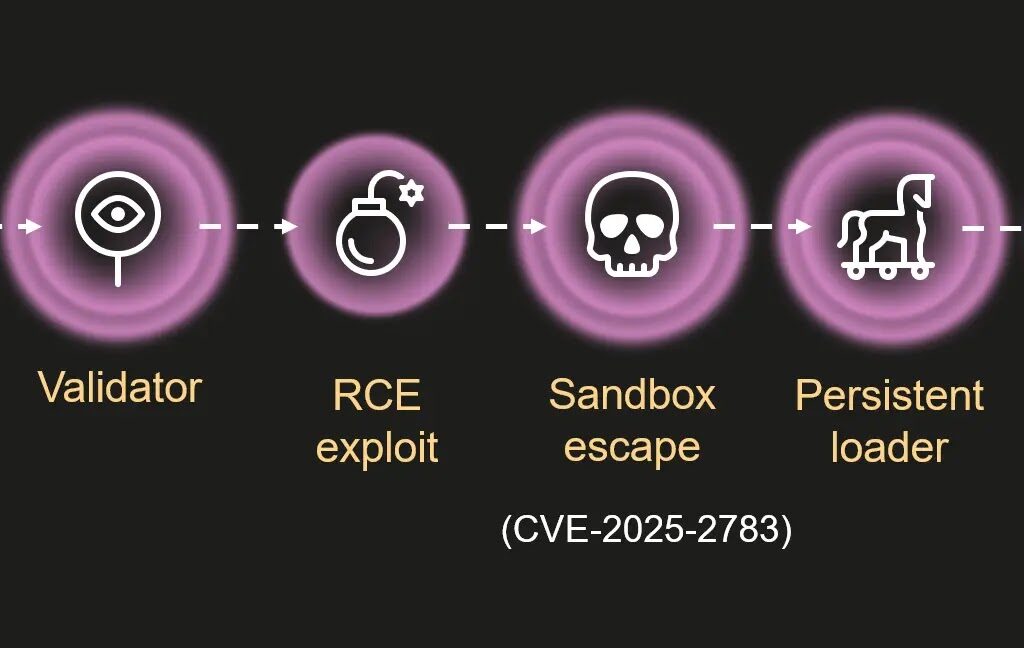
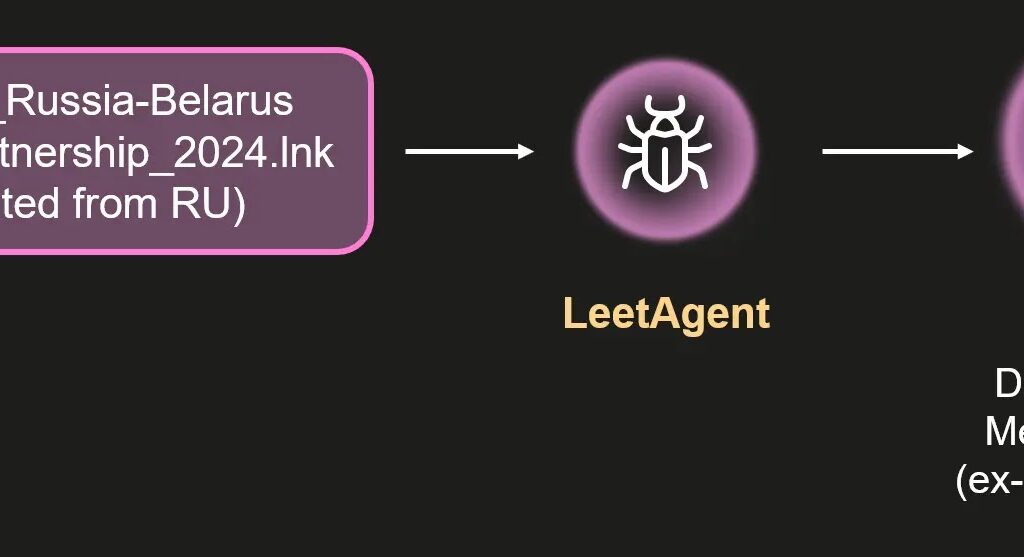
- Phishing Email Validation: The initial stage involved the delivery of a phishing email, crafted to appear legitimate. The attackers used WebGPU, a web graphics API, to confirm that the email was being read by a genuine browser rather than an automated scanner. This made it difficult for security software to detect the attack.
- Key Exchange and Payload Decryption: If the email was opened in a real browser, the attacker would initiate an elliptic-curve Diffie-Hellman key exchange. This secure key exchange mechanism was used to decrypt the next stage of the attack, which was hidden in benign-looking files like JavaScript bundles and fonts.
- RCE Exploit: A remote code execution (RCE) exploit was used to inject malicious code into the victim’s system. However, the key element that made this attack particularly dangerous was the ability to bypass Chrome’s sandbox using CVE-2025-2783. Once inside the sandbox, the attacker could hijack browser processes and inject a persistent loader.
- Persistence via COM Hijacking: The persistent loader used COM hijacking to override Windows registry entries for legitimate system files like twinapi.dll. This ensured that the malware would continue running even after the browser was closed or the system was rebooted.
- LeetAgent: A Rare Spyware: The loader eventually decrypted and deployed LeetAgent, a highly sophisticated piece of spyware. LeetAgent operated using “leetspeak” commands, which allowed it to conduct keylogging, steal sensitive documents (including PDFs and spreadsheets), and inject itself into other processes. The malware communicated with command-and-control (C2) servers over HTTPS, with traffic obfuscation pointing to commercial origins.
Connections to Memento Labs and Dante Spyware
The technical sophistication of LeetAgent led Kaspersky to link it to Memento Labs, an infamous Italian firm that has been tied to spyware development in the past. LeetAgent’s design bore similarities to Dante, a spyware tool unveiled at the 2023 ISS World conference and attributed to Memento Labs. Dante itself was a rebranded version of software originally developed by the notorious hacking firm Hacking Team.
Dante was known for its advanced obfuscation techniques, including VMProtect encryption, anti-debugging features, and dynamic API resolution to evade detection. The fact that LeetAgent shares code with Dante suggests that Mem3nt0 mori’s operations are closely tied to this commercial spyware market, which has proven resilient despite efforts to shut it down.
The Fallout and Response
After Kaspersky’s discovery, Google quickly issued a patch to fix the CVE-2025-2783 vulnerability in Chrome. Users are urged to update their browsers to version 134.0.6998.177 or later to mitigate the risk. Additionally, experts recommend enabling Chrome’s enhanced safe browsing feature and staying vigilant against phishing attempts, which remain the primary vector for these types of attacks.
Interestingly, Firefox also patched a similar inter-process communication flaw (CVE-2025-2857), highlighting that other browsers may be vulnerable to similar exploits. Security professionals are warning that the risk of pseudo-handle vulnerabilities could extend to other software, so vigilance is critical across all platforms.
The Bigger Picture: The Shadowy Spyware Market
The attack by Mem3nt0 mori underscores a deeper issue within the world of cyber espionage: the persistence of commercial spyware. Despite the closure of notorious firms like Hacking Team, their legacy lives on in the tools developed by companies like Memento Labs. These tools are being used by APT (Advanced Persistent Threat) groups to infiltrate and extract valuable intelligence from high-profile targets.
While the technical details of CVE-2025-2783 and the resulting malware campaign are concerning, they are only one part of the larger picture. As the spyware market continues to evolve, so too does the sophistication of the attacks carried out by groups like Mem3nt0 mori.
Staying Ahead of the Game
The Mem3nt0 mori attack serves as a reminder of the evolving nature of cyber threats and the importance of staying one step ahead in the digital arms race. While patching vulnerabilities is essential, it’s equally important to remain vigilant against phishing attacks, ensure browsers and software are up to date, and be aware of the techniques used by cybercriminals.
As we continue to navigate the cat-and-mouse game of digital espionage, understanding the methods behind these attacks is key to developing better defenses. Whether it’s through zero-day vulnerabilities, social engineering, or sophisticated spyware, the stakes are higher than ever in the battle for digital security.


Add a Comment