A new and highly polished campaign is targeting macOS users by cloning the Homebrew installation experience and quietly slipping malicious commands into victims’ clipboards. Instead of attacking Homebrew’s package repositories, attackers are impersonating the trusted installation page itself and hijacking the moment users paste the install command.
What’s happening
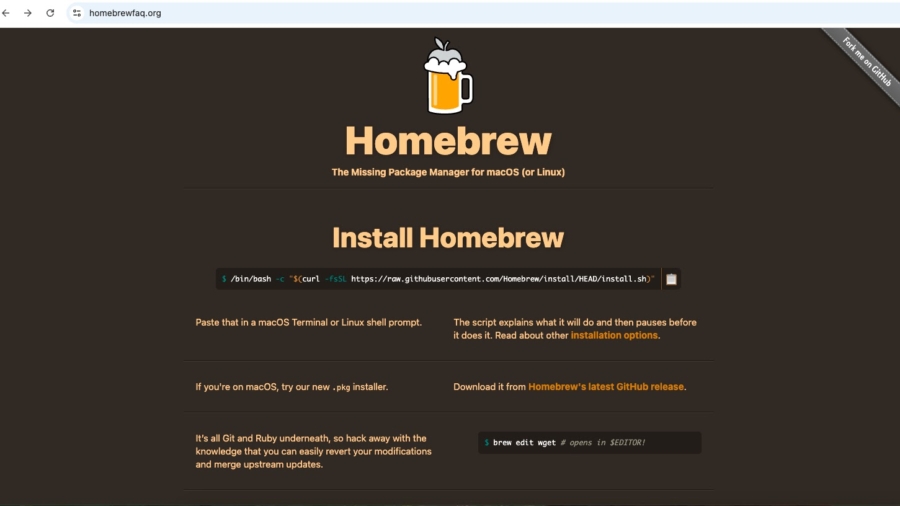
Researchers uncovered several pixel-perfect replicas of the official Homebrew installer page. Fraudulent domains identified include:
homebrewfaq[.]orghomebrewclubs[.]orghomebrewupdate[.]org
These sites look and behave like the genuine Homebrew install page, but they include hidden JavaScript that interferes with normal copy-and-paste behavior. Rather than allowing users to select the install command manually, the spoofed pages disable normal text selection and force visitors to click a site-provided Copy button. That button runs code which injects extra, malicious commands into the clipboard along with the legitimate Homebrew installer command.
How the attack works
- The attacker creates a convincing replica of the Homebrew install page so users won’t suspect anything is wrong.
- The page blocks standard selection and clipboard events (
contextmenu,selectstart,copy,cut,dragstart), preventing manual copying of the installation text. - A visible Copy button triggers a
copyInstallCommand()routine in JavaScript. That routine writes a command string to the clipboard using the Clipboard API or a textarea fallback for compatibility across browsers. - When the victim pastes that clipboard content into Terminal and runs it, the legitimate Homebrew install command executes but it’s accompanied by the attacker’s injected command(s), which download and run additional payloads in the background.
- Because the real Homebrew installer runs normally, the infection can be stealthy and persistent while appearing innocuous to the user.
Security analysts also noted Russian-language comments in the code showing where malicious commands are inserted — a sign this may be a commoditized service or a repeatable toolkit attackers can reuse.
Why this is notable
This campaign represents a significant shift in supply-chain style tactics. Instead of compromising package repositories or tampering with software packages directly, attackers have built a parallel interception point: the initial installation experience. That bypasses many defenses that focus on repository integrity and package signing, and it relies instead on social engineering and subtle client-side manipulation of the clipboard.
Homebrew itself has no recent compromise reports, but the attack exploits the strong user trust placed in Homebrew’s installation instructions.
For safety reasons I’ve redacted the exact malicious command observed in the wild. Publishing exact live payload commands or download URLs could enable abuse. If you need to analyze the specific artifacts for incident response, work with a trusted security team and obtain samples through secure channels.
Indicators and detection
Researchers identified the suspicious domains listed above and monitored infrastructure linked to known malware distribution networks. The telltale signs of this campaign include:
- Pixel-perfect replicas of the Homebrew installer page hosted on non-official domains.
- Disabled text selection and clipboard-related event handlers.
- A required on-page Copy button (rather than allowing manual selection).
- JavaScript routines that overwrite clipboard contents to append or prepend extra commands.

Add a Comment