The cybersecurity world has been rocked by the rise of the Trinity of Chaos, a highly sophisticated ransomware collective that has launched a new data leak site featuring sensitive information from 39 major corporations. This group, possibly a merger of notorious hacker groups like Lapsus$, Scattered Spider, and ShinyHunters, represents a significant evolution in the scale and complexity of cybercrime.
The Trinity of Chaos collective is not just another ransomware gang, it is a hybrid threat actor that merges traditional ransomware tactics with data extortion strategies, creating a new and highly effective form of attack. By combining these methods, they maximize their operational impact and financial return, leaving organizations exposed to both financial losses and reputational damage.
Data Leak Sites on the TOR Network
The group’s primary method of operation revolves around their Data Leak Site, hosted on the TOR network. This is a familiar tactic among modern ransomware groups, and Trinity of Chaos has refined it to a level of operational sophistication that sets them apart.
Rather than announcing new attacks or publicizing their ransom demands upfront, the group opts to share samples of stolen data, including sensitive records, to prove the success of their breaches. This approach not only validates their claims but also increases the pressure on their victims by threatening public exposure. This calculated strategy ensures the group maintains operational security while leveraging the threat of reputational harm to manipulate their targets into compliance.
Previous Salesforce Exploit and Data-Exfiltration Tactics
Trinity of Chaos has already demonstrated their ability to exploit Salesforce environments, a method they refined by exploiting compromised Salesloft Drift AI chat integrations. By using social engineering techniques, the group gains unauthorized access to OAuth tokens, which they then use to infiltrate corporate Salesforce environments. This precise and targeted approach has proven to be highly effective, leading to substantial data breaches and stolen records.
The leaked data from these campaigns primarily includes personally identifiable information, but also reveals internal communications, loyalty program data, and full activity histories. In addition to using this data for extortion, Trinity of Chaos has proven adept at using it for further social engineering campaigns, gaining additional leverage over both companies and individuals.
This particular method of attack prompted the FBI to issue a flash warning, cautioning organizations to monitor their Salesforce instances for signs of intrusion.
Major Corporations Hit
The scale of the breach is unprecedented. Among the compromised organizations are some of the world’s most recognizable names, including:
- Cisco
- Toyota Motor Corporation
- FedEx
- Disney/Hulu
- Home Depot
- Marriott
- McDonald’s
These companies, spanning a range of industries including technology, automotive, finance, and telecommunications, are now facing the prospect of massive data leaks unless negotiations with the hackers are met.
Pressure Tactics and Ultimatums
Trinity of Chaos has set October 10th as a hard deadline for negotiations. Like many traditional ransomware operations, the group employs psychological pressure tactics, leveraging the threat of public data exposure and even regulatory reporting that could lead to criminal negligence charges for non-compliant companies.
This combination of tactics heightens the stakes for organizations and forces them to make quick decisions under intense pressure.
A Treasure Trove for Cybercriminals
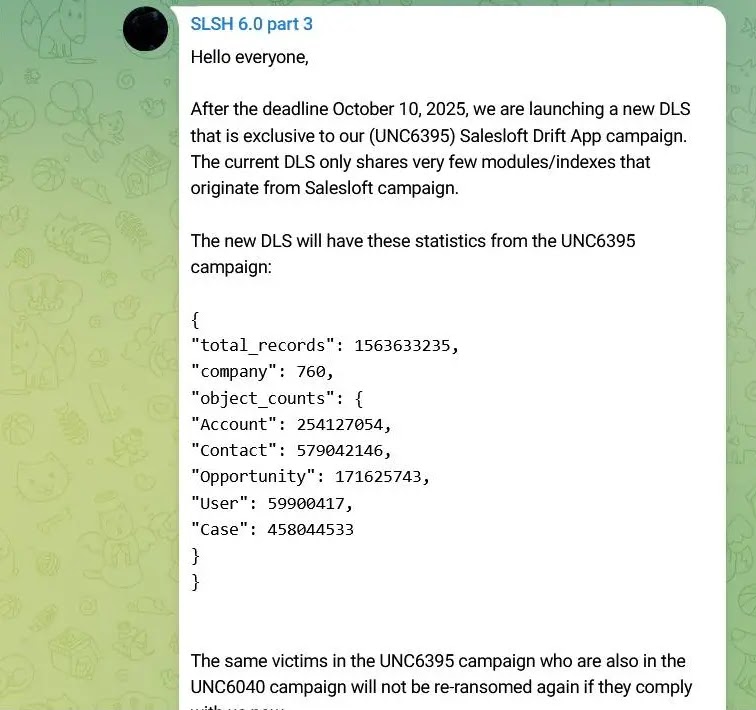
The Trinity of Chaos collective claims to have amassed an incredible 1.5 billion records from over 760 companies, including:
- 254 million account records
- 579 million contact entries
- 458 million case files
This data, collected over several years, comes from previous attack campaigns such as UNC6395 and UNC6040, showcasing the group’s systematic approach to data aggregation and monetization.
By compiling vast databases of stolen records, Trinity of Chaos is building a cybercrime empire with an unprecedented level of access to sensitive corporate and personal information.
Sophistication and Operational Security
What sets Trinity of Chaos apart is their operational security. The group is known to maintain persistent access within victim networks for extended periods of time, often remaining undetected for years.
This long-term, stealthy approach is indicative of a highly disciplined and experienced group, with extensive operational infrastructure that allows them to scale and evolve their methods over time.
The Rise of a Hybrid Cybercrime Syndicate
The Trinity of Chaos collective marks a significant evolution in the world of cybercrime. By blending ransomware tactics with data extortion and leveraging the TOR network for secure communications and leak sites, they are raising the stakes for both organizations and the cybersecurity industry at large. With an impressive track record, a global reach, and an ever-growing arsenal of attack methods, this group represents a formidable challenge to the cybersecurity landscape.
Organizations are urged to stay vigilant, fortify their defenses, and remain proactive in addressing any potential threats to prevent becoming the next victim of this highly skilled and resourceful group.


Add a Comment