A new and highly advanced banking Trojan, dubbed Maverick, has surfaced in Brazil, exploiting WhatsApp as its main vector to compromise thousands of unsuspecting users. First detected in mid-October 2025, Maverick has already triggered over 62,000 blocked infection attempts within just the first ten days, signaling a significant threat to Brazilian internet users
Maverick targets Brazilian users by sending Portuguese-language WhatsApp messages that include malicious ZIP archives. These archives cleverly bypass WhatsApp’s security filters and contain a weaponized .LNK file, a Windows shortcut file that acts as the Trojan’s entry point.
The infection process begins when victims open these ZIP files, often disguised as bank notifications or important documents. The .LNK file then launches a chain of commands through cmd.exe and PowerShell, connecting stealthily to command-and-control (C2) servers. These servers validate the malware with stringent authentication protocols before downloading additional payloads.
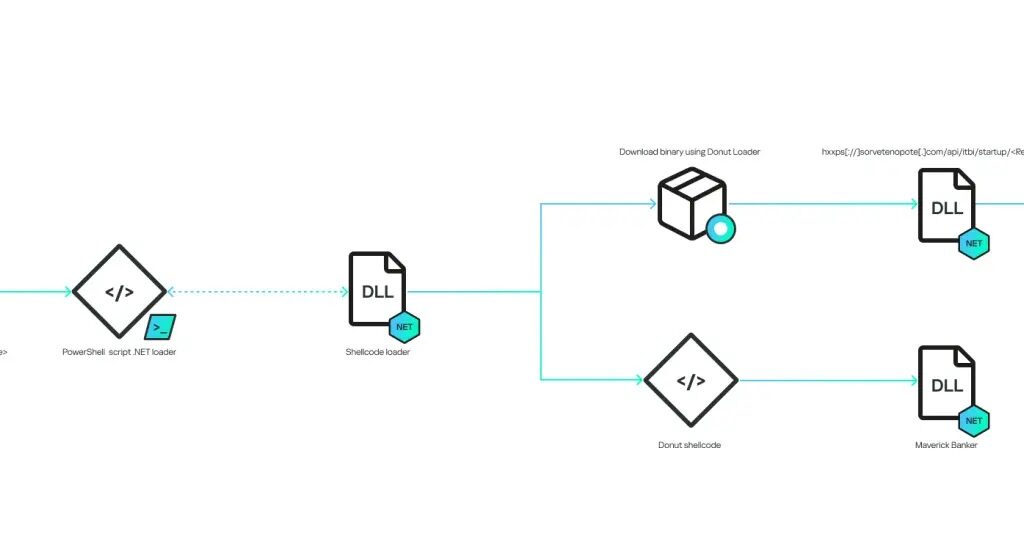
What makes Maverick especially dangerous is that it operates in a fully fileless manner, all malicious components run directly in the system’s memory without writing files to the disk. This approach makes detection by traditional antivirus tools extremely difficult.
An Evolution in Malware Development: AI-Assisted Coding
Researchers at Securelist have found that Maverick shares significant code overlap with Coyote, a Brazilian banking Trojan documented in 2024. However, Maverick is more sophisticated, notably due to its use of artificial intelligence during its development. AI techniques are leveraged particularly for decrypting security certificates and optimizing the malware’s code-writing process.
This marks a worrying trend where cybercriminals are integrating AI tools to create more potent and evasive malware, raising the stakes in the cybersecurity battle.
Confirming the Victim’s Location
Maverick includes stringent geographic targeting measures to avoid detection and ensure attacks focus solely on Brazilian users. The malware checks:
- System timezone
- System language
- Region settings
- Date format
If any of these indicators do not confirm a Brazilian environment, the malware immediately terminates, preventing analysis by security researchers outside Brazil.
Spyware Capabilities and Data Theft
Once activated, Maverick unleashes an arsenal of surveillance tools:
- Capturing screenshots
- Monitoring browsers
- Logging keystrokes
- Controlling the mouse
- Displaying overlay phishing pages
These tactics target credentials from 26 Brazilian banks, six cryptocurrency exchanges, and one payment platform, aiming to steal sensitive financial information and take over accounts.
Self-Propagation Through WhatsApp Account Hijacking
Perhaps the most alarming feature of Maverick is its ability to self-propagate by hijacking infected users’ WhatsApp accounts. Using WPPConnect, an open-source WhatsApp Web automation framework, the malware automatically sends malicious messages to all contacts in the victim’s list.
This worm-like behavior allows the Trojan to spread rapidly and exponentially, leveraging WhatsApp’s massive user base as a distribution network.
Advanced Command-and-Control Security
Maverick’s C2 infrastructure employs sophisticated security measures to avoid detection and tampering:
- HMAC-256 signatures authenticate each request with a hardcoded secret key:
"MaverickZapBot2025SecretKey12345". - Validation of User-Agent headers ensures that only genuine malware clients connect.
- API endpoints deliver payloads encrypted as shellcodes using Donut loaders, with XOR encryption keys cleverly hidden within the payload’s final bytes.
The malware’s decryption method extracts the encryption key from the payload itself by reading the last four bytes to determine key size and then applying XOR operations to decrypt the entire code. Additionally, heavy code obfuscation techniques, such as Control Flow Flattening, make reverse engineering and analysis extremely challenging.


